Table of Contents
QuSmart.AI Infinity Engine Azure Documentation - GPU
Network Diagram
QuSmart.AI Infinity Engine Topology
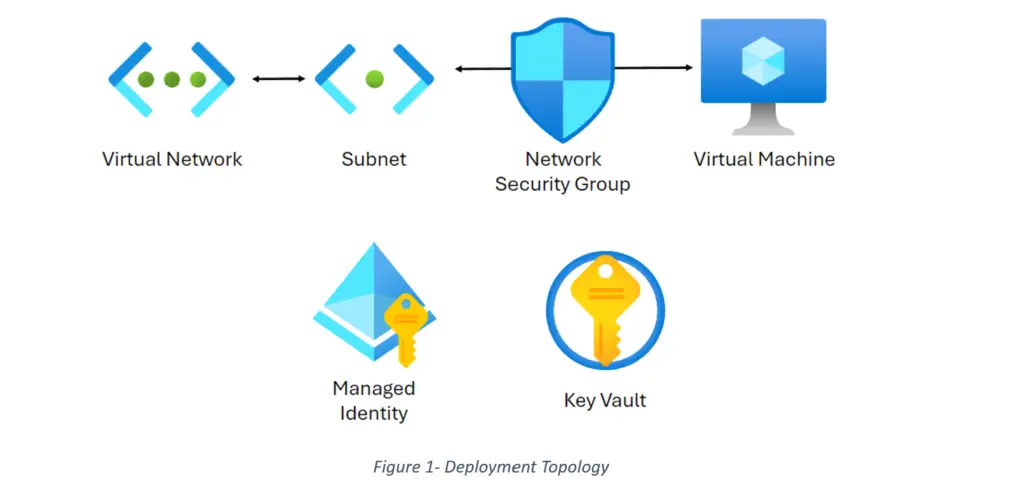
The Publisher only has Just In Time access granted by the customer to the Virtual Machine, the Managed Identity, the Key Vault with the secret, the Network Security Group, the subnet, and the Virtual Network.
Key Vault Preconfiguration
The key vault is deployed with soft delete and purge protection. Azure makes multiple redundant copies of your key vault. It is a best practice for customers to make a backup and a glass key of the secret in the key vault that ignites the engine. Learn More about the importance of your secret for disaster recovery.
Supported Azure VMs:
The preconfigured option deploys a Standard_NC4as_T4_v3 with 4 vCPUs and a NVIDIA T4 GPU. There are 4 compatible sizes for this offering:
The 4 vCPU allows customers to encrypt and decrypt 2,000 TB (2 PB) a month. [Standard_NC4as_T4_v3]
The 8 vCPU allows customers to encrypt and decrypt 4,000 TB (4 PB) a month. [Standard_NC8as_T4_v3]
The 16 vCPU allows customers to encrypt and decrypt 8,000 TB (8 PB) a month. [Standard_NC16as_T4_v3]
The 64 vCPU allows customers to encrypt and decrypt 33,000 TB (33 PB) a month. [Standard_NC64as_T4_v3]
Introduction
Discover the ultimate in data protection with QuSmart.AI’s Infinity Engine. Our solution seamlessly integrates with both Linux and Windows operating systems, ensuring your data remains secure with the highest level of encryption—perfect secrecy.
Features
- Seamless Integration: Compatible with Linux/Windows operating systems.
- Dynamic Encryption: Each TCP/IP session uses a new encryption method.
- AI-Driven: No need to manage encryption keys; our AI handles it all.
- Versatile Data Support: Encrypts any data type, including database dumps, full backups, and critical files.
Product Details
Service Ports:
| Service | Port | Comment |
|---|---|---|
| Perfect Secrecy Encryption | 8081 | Asynchronous Encryption service |
| Perfect Secrecy Decryption | 8082 | Asynchronous Decryption service |
- Encryption & Decryption: Data sent to the encryption port (8081) is returned encrypted, while data sent to the decryption port (8082) is returned in its original form.
- Corruption Detection: Ensures data integrity by rejecting corrupted files.
How It Works
Encryption Example:
nc {EaaS_IP} 8081 < inputfile > outputfile.enc
Encrypts inputfile and outputs the encrypted content as outputfile.enc.
Decryption Example:
nc {EaaS_IP} 8082 < outputfile.enc > inputfile
Restores the original file format from outputfile.enc.
- No Key Management: The AI system automatically handles encryption and decryption.
- Corruption Handling: Stops encryption and decryption if corruption is detected, ensuring data integrity.
QuSmart.AI is a women-founded Quantum Security company with patent pending technology for perfect secrecy solutions that are quantum-secure AI solutions.